Is Your Board Prepared for New Cybersecurity Regulations?
CFO News Room
NOVEMBER 12, 2022
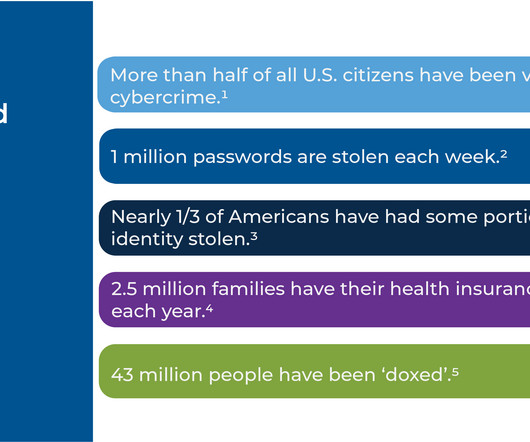
Boards are now paying attention to the need to participate in cybersecurity oversight. Boards have a particularly important role to ensure appropriate management of cyber risk as part of their fiduciary and oversight role. Not only are the consequences sparking concern, but the new regulations are upping the ante and changing the game.






















Let's personalize your content